Wireshark is a network protocol (packet) analyzer.It will help us in network troubleshooting,understanding how nmap scans and protocols work.
Common uses of Wireshark:
-
Capturing real-time network data
-
Importing data packets from text files
-
Examining data packets and their protocol details
-
Displaying, filtering, and searching data packets
-
Colorizing data packets
-
Troubleshooting network problems
-
Generating statistics
-
- Do not use wireshark with root privileges,To use it without root add your ’user’, to the ’wireshark group’.
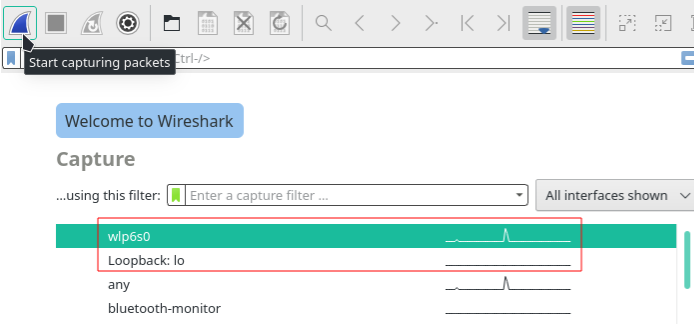
Select your network device interface and press ‘bluefin’ button to see network traffic.
Click on settings(screw) button to get details of your network interface.’Lifelines’ shows there’s traffic flowing through the following interface.
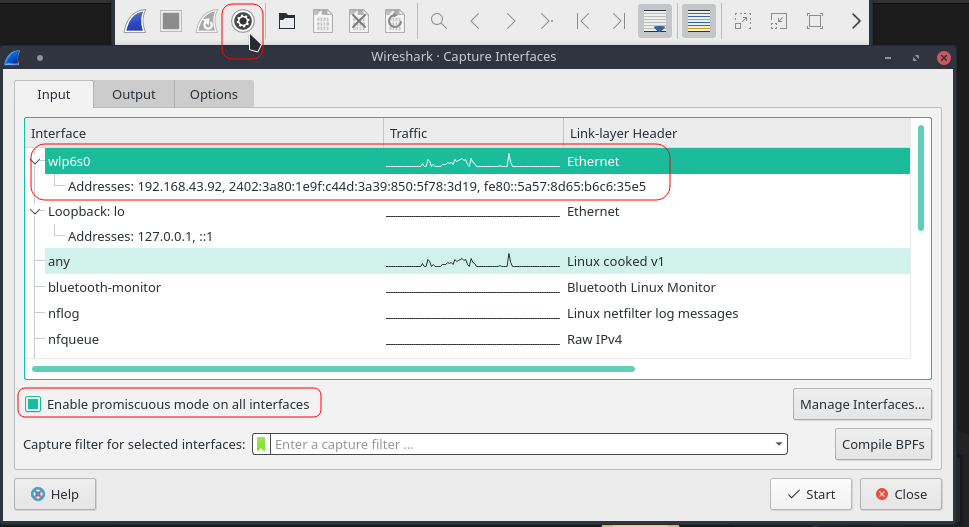
By default promiscuous mode is enabled meaning wireshark will receive all traffic on the network.Enabling it allows us to view all the packets on the network without limiting to the packets associated with our network adapter.
Filtering packets
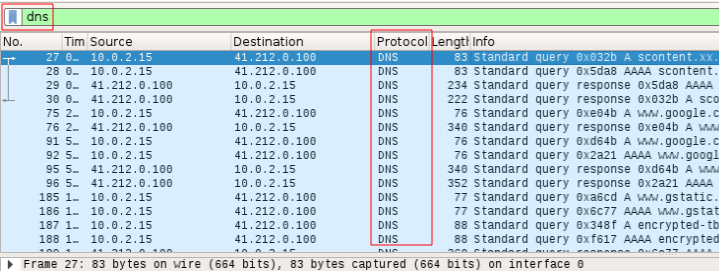
If you want to investigate something specific(like a protocol), you can use the Wireshark filter option. A basic method of filtering packets is to use the filter box on the upper section of the tool.For example, if you want to see the results of only DNS traffic, write "dns”.
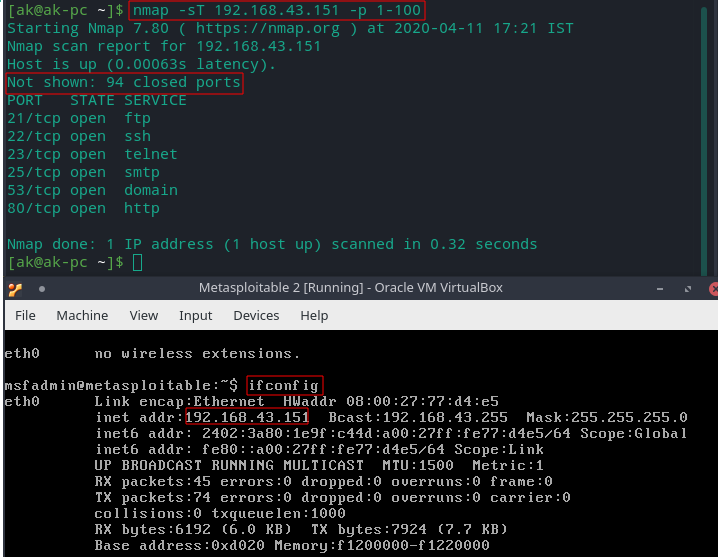
1. Nmap TCP Connect scan
In it we establish a connection with the target by issuing the “connect” system call.But the problem with this scan is that it takes time to complete and it require to generate more packets to obtain information.On the other hand, targets are more likely to allow the connection because it tries to establish a connection with target same as network enabled applications like web browsers.TCP Connect Scan sends a ACK packet and establish the connection.After it establish the connection, it resets the connection.
Syntax:
nmap -sT [TARGET] -p [PORT RANGES]
Adding -p option will scan only specified ports.
Metasploitable2 TCP connect scan of ports 1 to 100
Wireshark Output of the scan
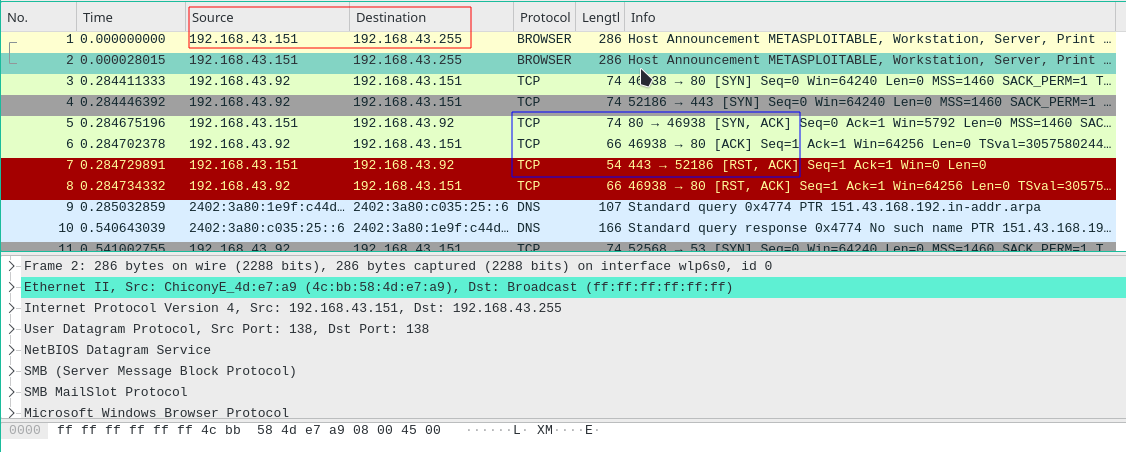
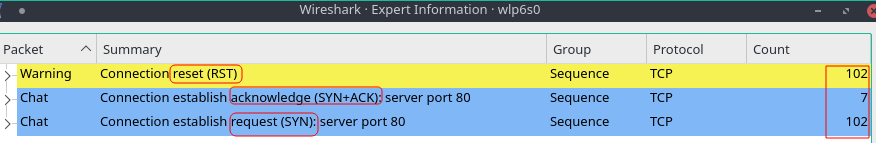
- Above we can see the traffic going back and forth between our machine(192.x.x.92) and metasploitable2(192.x.x.151).
Meaning of the default Wireshark colors:
Behind the scenes:
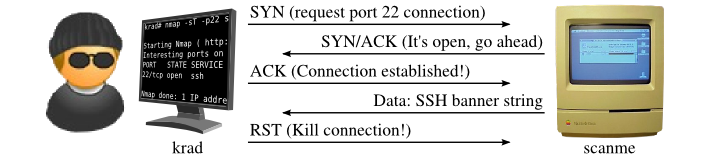
Here nmap is completing a TCP Three-Way Handshake.When we connect to each port we are using the TCP Protocol to transmit data between our machine and metasploitable2.
TCP 3-way handshake :
-
We are using TCP Protocol to send a packet with the SYN flag set =[SYN] (Synchronize Sequence Number).It informs Metasploitable2(Meta2) that we will start communication and the sequence number we start segments with.
-
Then we get a [SYN, ACK] flag back, it means Meta2 acknowledges that the port is open.
Acknowledgement(ACK) signifies the response of segment it received and SYN signifies with what sequence number it is likely to start the segments with. -
We will send back the [ACK] flag to acknowledge the response of metasploitable2 and we establish a reliable connection.
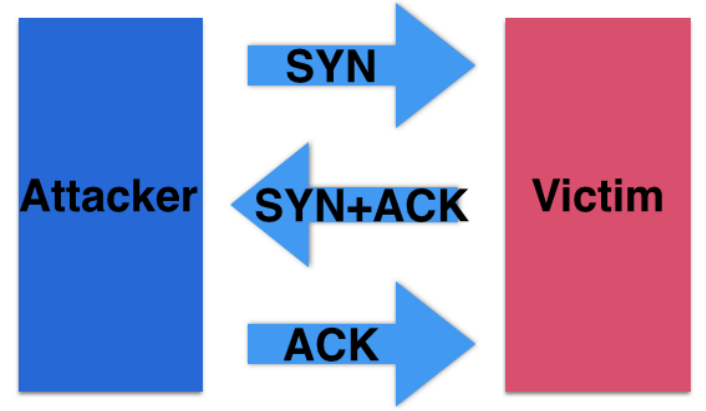
- [RST] is for resetting the connection. It is used when a TCP end detects errors on connection and these errors cannot be recovered from any TCP recovery method ( re transmissions etc) .Here TCP layer reset the connection (terminate the connection) , so that there can be a fresh start.
2. Nmap TCP SYN(stealth) scan
It help us to be little less noisy and covert about our scanning.
- Most popular and default scan
- Performs quickly and less likely to get block from firewalls
- When it comes to port states - open,closed and filtered ,TCP SYN scan gives a clear definition.
- It works on TPC 3-way handshake and requires raw-packet privileges that need root access.
Open State:
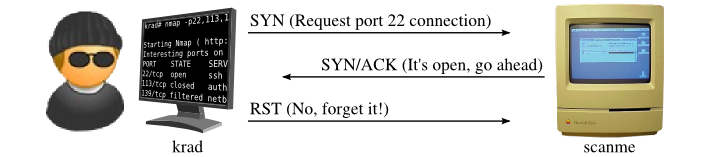
Here we try to establish a connection with target by sending TCP SYN packet. In this situation server sends a SYN/ACK packets to establish the connection.This is the result that Nmap uses to determine whether the port is open. Nmap reset the connection at the end.
Close state:
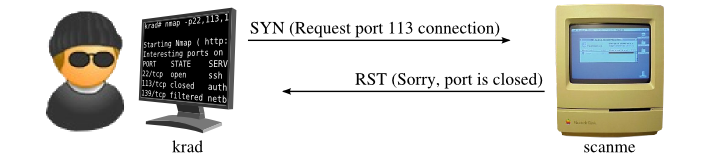
TCP SYN packet is send to the target as the last time and what happened here is target directly reject the connection with RST packet due to the closed port.
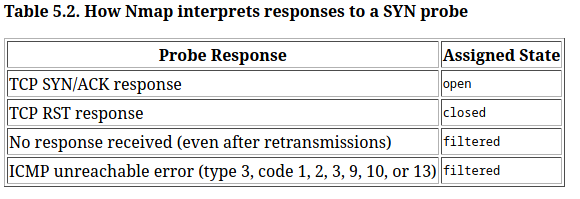
Filtered port:

Target doesn't sends a reply back,not even a RST packet to terminate the connection. Most accurate reason can be a firewall on the target side blocks reply packets. So nmap decides this type of ports as filtered.
Syntax:
nmap -sS [TARGET] -p [PORT RANGES]
Metasploitable 2 TCP SYN(Stealth) scan of ports 1 to 100
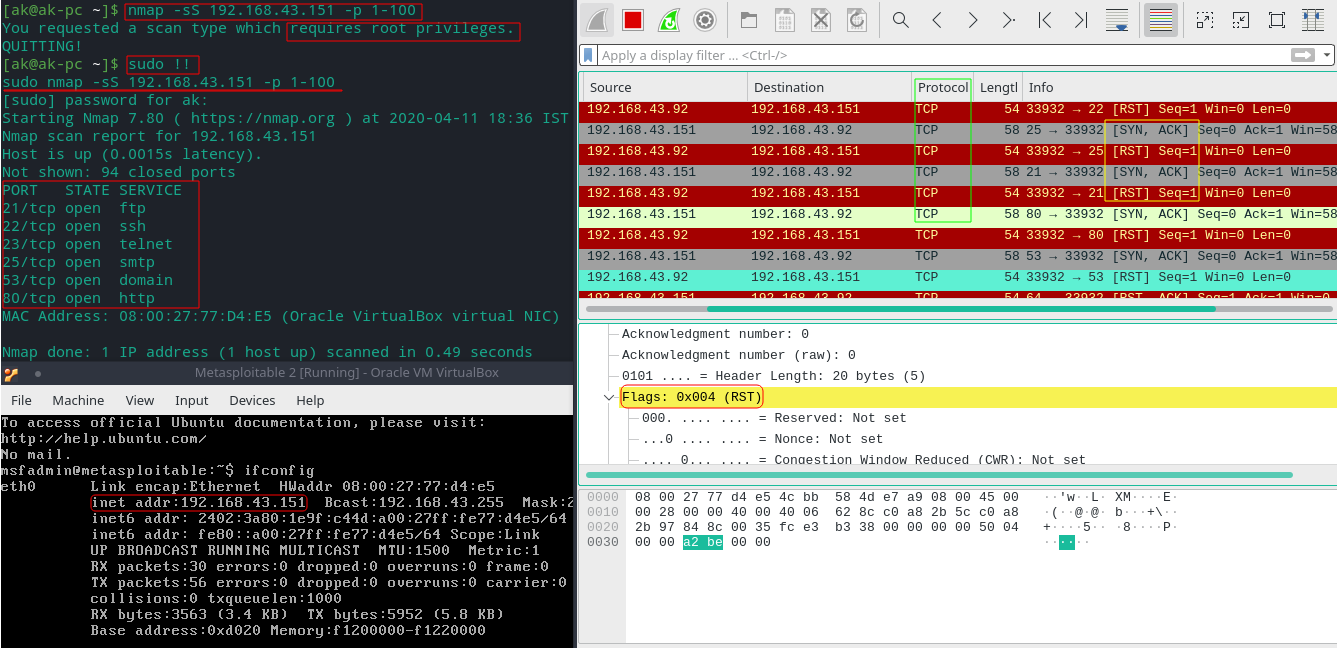
In this scan nmap prevent the completing of the TCP 3-way handshake to avoid raising any alarm bells. It first sends the [SYN] flag and receive [SYN, ACK] flag back. After that it sends the [RST]=Reset flag back (highlighted in red) which prematurely terminates the connection.
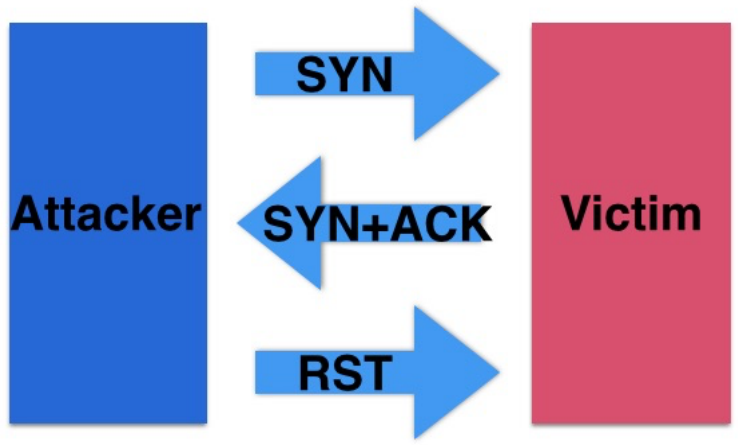
- Therefore in the log files it no longer show that a TCP 3-way handshake was completed and we are less likely to be blocked by an IPS (Intrusion Detection System).
- TCP Connect scan establish a full connection with the target but SYN scan completes only a half of the connection with target.
Note: SYN Scan is not stealthy anymore. Widely deployed intrusion detection systems and personal firewalls are quite capable of detecting default SYN scans.